
5th ASTIN Cyber Workshop (ACW) Meeting: An Overview of Current Topics in the Cyber Insurance Market
On October 31st, 2022, over 80 participants from cyber (re)insurers, policymakers, intermediaries, cyber security, and related industries, as well as academic researchers and other interested parties, gathered at the Old Library in the basement of the Lloyds’s building. Beside networking and an open exchange of ideas during lunch and after event networking drinks, the agenda of the day was focused on several most current and key cyber topics, of which we will give a brief overview in this article. In the following weeks, we will feature speakers and topics in more depth on Cyber-Economics.com.
Damages & Claims Update
Opening the session, Sie Liang Lau from SCOR, welcomed the guests and introduced the events. He highlighted the developments observed in the market in the last six months as follows:

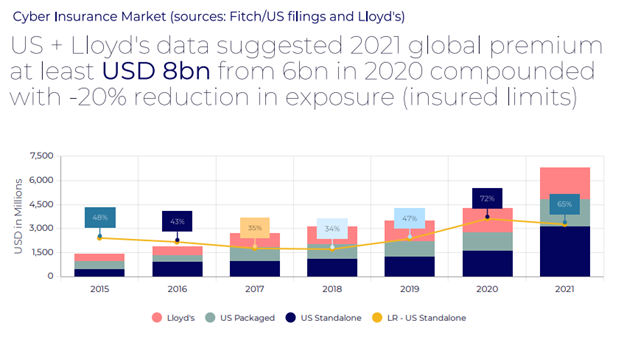
Regarding claims, he showcased the recent numbers of US markets, Lloyds, and others combined for the previous year. The global premium is estimated at $8bn for 2021, up from $6bn in 2020. The loss ratio of US standalone decreased from 72% in 2020 to 65% in 2021.
In the damages update section, Sally Adam from Sophos gave new insights from the UK-based IT security company.
“One of the most significant developments over the last year is the development and professionalization of the cyberthreat economy. Individual gangs are specializing in a particular area – initial access, ransomware, information-stealing malware etc. – and offering it as a service to other criminals. Someone described it to me the other day as the ‘Amazon of cybercrime’.
The big problem for all of us on the right side is that these service models lower the bar, allowing less skilled individuals to enter the malware world, increasing the number of adversaries and attacks.”
In addition, adversaries attempt to avoid detection by security technologies by exploiting posture weaknesses, stolen access data, and legitimate IT tools among increasing professionalism and scalability of cybercrime.
On the Insurance specific claims update, Gallagher Re’s Ed Pocock, and Jennifer Braney showcased how past and on-going adjustments and improvements in underwriting, rate increases and additional technology have driven the loss ratio to an estimated 42% for an exemplary generic model portfolio in 2022.

Academic Research
To represent the many colors of academic research into cyber insurance and related topics, three papers were presented early in the day to facilitate the networking between research and the present industry stakeholders.
Dr. Daniel Woods explained his past and recent research activities, currently at the University of Edinburgh. We highly recommend his Researchgate Page, where you can find most of his papers and a good overview.
Dr. Leonie Ruderer from R+V Versicherung and Jonas Becker from Munich Re presented their paper that is currently in its finalisation steps and created within the Cyber Working Group of the German Actuary Association (DAV). The paper “Use Case der DAV AG Daten und Methoden zur Bewertung von Cyberrisiken” will be soon published on www.aktuar.de aims to establish a pricing of a SME Cyber Product in Primary Insurance with a focus on expected loss. The threat scenarios are focused on Ransomware and modelled with an extreme value statistics approach. An accompanying R script will also be made available.
Yousra Cherkaoui Tangi couldn’t make it in person due to visa issues. As a rather poor standin, yours truly explained the broad strokes of the paper, in which she modelled cyber-attacks using Hawkes Processes.
Clauses
The war clause debate with a live panel of Peter Wedge (Swiss Re), Helga Munger (Munich Re), Rory Egan (AON), Peter Hacker (Cyber Risk Observatory), moderated by Sie Liang Lau (SCOR), was a lively and extremely insightful discussion between experienced industry stakeholders that are facing a regulatory “external shock” in the form of the recently introduced systematic cyber operation/war exclusions that were mandated by Lloyds and other markets.

In many parts, de jure nature of the discussion for the half a dozen clauses were focussed on the clarity of the wordings in ensuring cyber operation as part of war is excluded. The market is flooded with many versions since LMA’s and the debate is around the effectiveness of some of the definitions introduced especially on attribution whereby for some panel is still subject to court interpretation ultimately. This attribution question has often tremendous practical implications, as without a clear naming of the specific, independent body or entity that makes such attribution, a situation like notPetya in 2017 could arise again, where the widely believed Russian sponsored attack was never officially acknowledged as such by the perpetrator. We will feature this topic, as many others mentioned, more in depth with follow-up content.
Modelling Update & Model Divergence
As is almost tradition by this point, the committee asked the cyber risk modelers to provide PML approximations for several different return periods ranging from 1-in-10 to 1-in-250 of a sample portfolio consisting of about 600 firms, concentrated more in the large cap sector. CyberCube, Cyence (Guidewire), and RMS providing data samples.
While we will have a detailed look on the data in the leadup to the Cologne Cyber Insurance Hackathon as described below, with accompanying articles on cyber-economics.com, a main point of discussion the persisting divergence between models, especially in the long tails from 1-in-100 years on-wards. The topic is certainly double-edged, as it on the hand demonstrates a healthy eco-system where firms are confident to share their honest estimates without considering herding, but on the other hand demonstrates a still fundamental prognostic and divergent challenge.

Echoing these concerns, AON presented a chart that featured three anonymous modelers and their predictions on average annual losses (AAL) up to extreme scenario of 1-in-250 years losses with regards to an additional exclusion in the systematic cloud outage in the underlying policies. Model 2 drops their losses by up to 30%, with a baseline of 20%, while Model 3 barely registers the exclusions with an overall 5% reduction.

Cyber ILS
For the Insurance Linked Securities portion of the event, California-based DeNexus, presented their in-side out IOT-based approach to tackle, among others, the accumulation risk that would be a potential trigger for a cyber-ILS transaction and how it can be tamed.

Regarding the overall market for cyber ILS, that has as of now only seen a few private deals and cyber as part of a much larger risk portfolio that was ceded, AON summarized the current situation and necessary adaptions for the next step:
- There is a sustained demand for ILS capacity and a nascent market.
- Constraints in product structure exist but are not insurmountable.
- The competition for capacity is fierce, so the cyber market needs to educate investors of the capital markets.
- Structural changes to the cyber modelling market are required to fully unlock the potential of the capital.
Alex Mican of Verisk PCS contributed to the Cyber ILS portion of the workshop by presenting the work done on a PCS global Cyber Industry Exposure Database. They started off with a database of 400+ affirmative cyber programs, estimating an overview of ~80% of the Global Cyber Insurance Market in excess of $100 million. This generated a consensus view of the number of companies and aggregate limit available in the market by limit bands ($500+m; $3-499m; $2-299m; $1-199m; $35-99m; <$35m) at a point in time – Sept 2022. The PCS IED will be further refined and interested parties are encouraged to participate in order to get the contents of the IED themselves.
Follow Up: #1 Cologne Cyber Insurance Hackathon, January 20th 2023
On January 20th SCOR will host the #1 Cologne Cyber Insurance Hackathon at the SCOR office in Cologne, Germany.
The clear and not at all easy to duck out goal is to “produce something tangible” with the data given by the risk modelers at the ASTIN event, academic research, cyber damage databases, claims data donated by insurers or MGAs or the plethora of other options. With 40 participants in attendance and a live stream to Linkedin, and, even though we do not know exactly how yet, someway to participate from home, we this type of “Hackathon” as the natural and logical continuation of our more market focused ASTIN events at Lloyds.
As this might very easily go off-rails in the about 8 or so quality working hours on the day, there will be rigorous preparations to make the day a success and achieve the ultimate goal: ”Something tangible”, so stay tuned!
As to the next instance of the ASTIN Cyber Meeting at Lloyds, we are currently eyeing April 2023 for the 6th Edition. Certainly, the half year in between then and now, and a very interesting renewal phase, will provide further interesting discussions.
In between, we will use cyber-economics.com to bring this summary and other discussed topics to a wider audience.
We would like to thank all the participants and may the next one be a smashing success as this one!
Sie Lau, Alex Mican, Daniel Kasper

Daniel Kasper
Daniel Kasper is the principal of Cyber Economics.










